Kaspersky experts have discovered that the most commonly used protocol for transferring data from wearable devices used for remote patient monitoring contained 33 vulnerabilities, including 18 “critical vulnerabilities” in 2021 alone. This is 10 more critical vulnerabilities than in 2020, and many of them remain unpatched. Some of these vulnerabilities give attackers the potential to intercept data being sent online from the device.
The ongoing pandemic has led to a rapid digitalization of the healthcare sector. With hospitals and healthcare staff overwhelmed, and many people quarantined at home, organizations have been forced to rethink how patient care is delivered. In fact, recent Kaspersky research found that 91% of global healthcare providers have implemented telehealth capabilities. However, this rapid digitalization has created new security risks, especially when it comes to patient data.
Part of telehealth includes remote patient monitoring, which is done using so-called wearable devices and monitors. These include gadgets that can continuously or at intervals track a patient's health indicators, such as cardiac activity.
The MQTT protocol is the most common protocol for transmitting data from wearable devices and sensors because it’s easy and convenient. That’s why it can be found not only in wearable devices, but also in almost any smart gadget. Unfortunately, when using MQTT, authentication is completely optional and rarely includes encryption. This makes MQTT highly susceptible to man in the middle attacks (when attackers can place themselves between “two parties” while they communicate), meaning any data transferred over the internet could potentially be stolen. When it comes to wearable devices, that information could include highly sensitive medical data, personal information, and even a person’s movements.
Since 2014, 90 vulnerabilities in MQTT have been discovered, including critical, many of which remain unpatched to this day. In 2021, there were 33 newly discovered vulnerabilities, including 18 critical ones—10 more than in 2020. All of these vulnerabilities put patients at risk of having their data stolen.
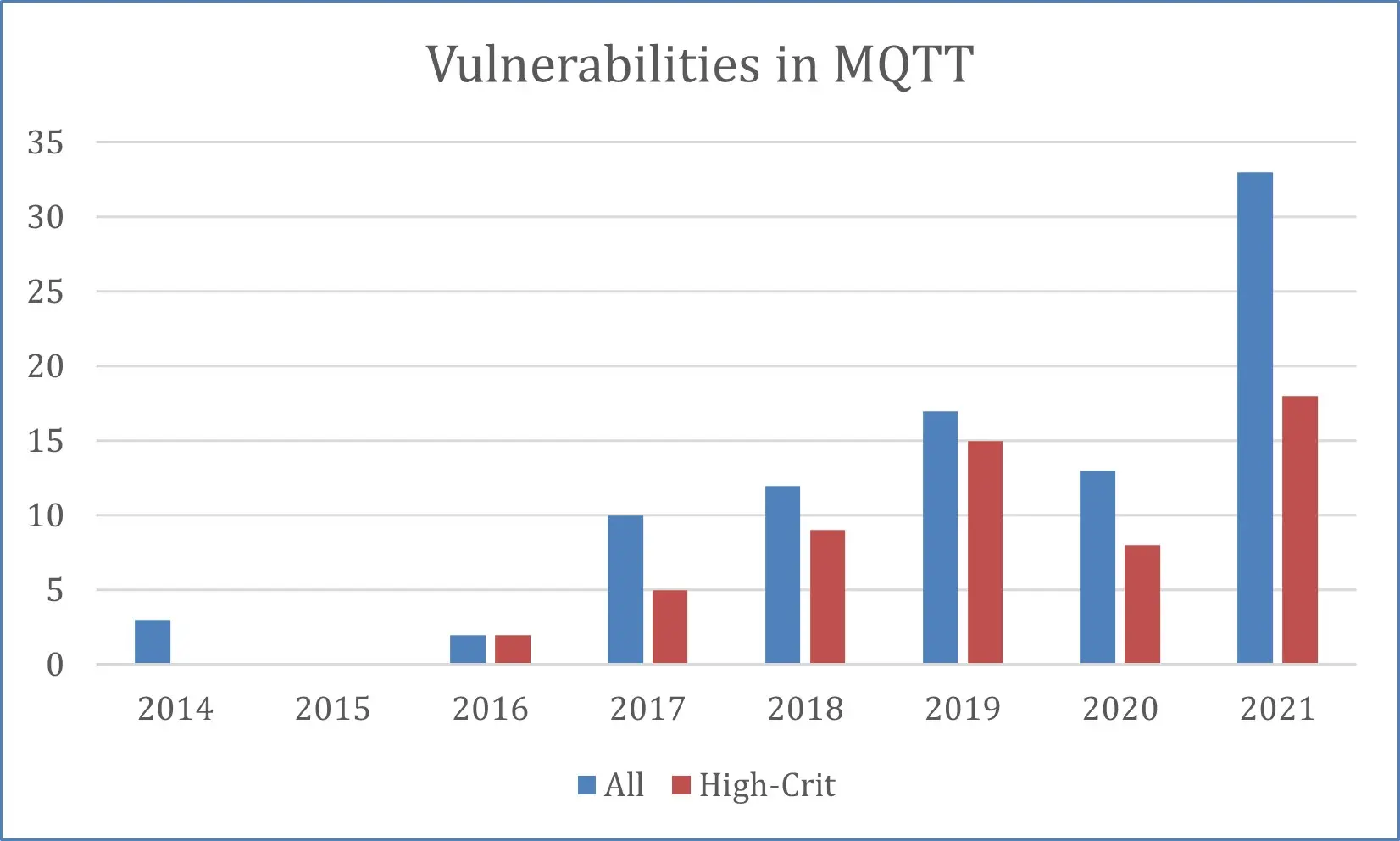

Number of vulnerabilities found in the MQTT protocol, 2014-2021
Kaspersky researchers found vulnerabilities not only in the MQTT protocol but also one of the most popular platforms for wearable devices: the Qualcomm Snapdragon Wearable platform. There have been more than 400 vulnerabilities found since the platform was launched; not all have been patched, including some from 2020.
It’s worth noting that most wearable devices track both your health data and your location and movements. This opens up the possibility of not just stealing data but also potentially stalking.
“The pandemic has led to a sharp growth in the telehealth market, and this doesn’t just involve communicating with your doctor via video software. We’re talking about a whole range of complex, rapidly evolving technologies and products, including specialized applications, wearable devices, implantable sensors, and cloud-based databases. However, many hospitals are still using untested third-party services to store patient data, and vulnerabilities in healthcare wearable devices and sensors remain open. Before implementing such devices, learn as much as you can about their level of security to keep the data of your company and your patients safe,” comments Maria Namestnikova, Head of the Russian Global Research and Analysis Team (GReAT) at Kaspersky.
Read the full report about the telehealth security on Securelist.
To gain more insights about the global adoption of telehealth services, read Kaspersky’s global survey.
To keep patient data safe, Kaspersky recommends that healthcare providers:
- Check the security of the application or device suggested by the hospital or medical organization
- Minimize the data transferred by telehealth apps if possible (e.g. don’t let the device send the location data if it’s not needed)
- Change passwords from default ones and use encryption if the device offers this
-Ends-
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com
© Press Release 2022
Disclaimer: The contents of this press release was provided from an external third party provider. This website is not responsible for, and does not control, such external content. This content is provided on an “as is” and “as available” basis and has not been edited in any way. Neither this website nor our affiliates guarantee the accuracy of or endorse the views or opinions expressed in this press release.
The press release is provided for informational purposes only. The content does not provide tax, legal or investment advice or opinion regarding the suitability, value or profitability of any particular security, portfolio or investment strategy. Neither this website nor our affiliates shall be liable for any errors or inaccuracies in the content, or for any actions taken by you in reliance thereon. You expressly agree that your use of the information within this article is at your sole risk.
To the fullest extent permitted by applicable law, this website, its parent company, its subsidiaries, its affiliates and the respective shareholders, directors, officers, employees, agents, advertisers, content providers and licensors will not be liable (jointly or severally) to you for any direct, indirect, consequential, special, incidental, punitive or exemplary damages, including without limitation, lost profits, lost savings and lost revenues, whether in negligence, tort, contract or any other theory of liability, even if the parties have been advised of the possibility or could have foreseen any such damages.



















