- Check Point Research (CPR) has analyzed the files that are for sale on the Dark Web, whose sellers claim are from WhatsApp users, revealing the leak includes 360 million phone numbers from 108 countries
- Users are advised to be aware of links and unknown senders, while using any messaging services
Following reports that hackers were selling WhatsApp numbers on the Dark Web (please note CPR cannot confirm or proof these numbers are from WhatsApp users), CPR researchers decided to analyze these and revealed the leak contains 360 million phone numbers of WhatsApp users from 108 countries.
Each country has a different number of records that have been exposed, ranging from 604 in Bosnia and Herzegovina to 35 million attributed to Italy. Approximately 5.3 million phone numbers have been leaked from the United Arab Emirates. In the past four days the files, which include international dial codes and were for first set for sale, are now being distributed freely amongst hackers.

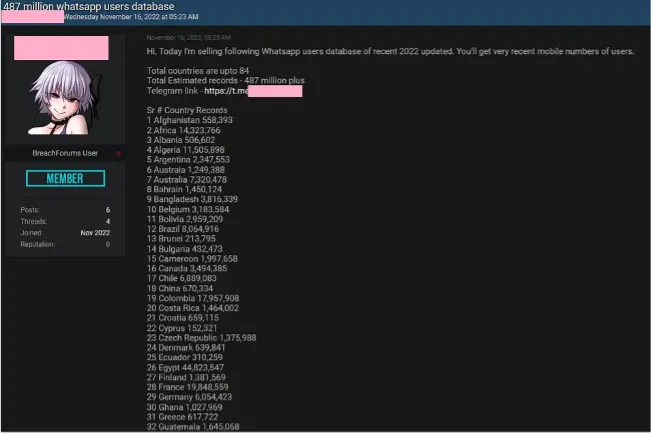
The news about these files being sold on the Dark Web was first exposed on November 16th in a msg. published by the Hacker on the hacking forum BreachForums, claiming to be selling up-to-date personal information of 487 million WhatsApp users from 84 countries.

Source: Dark Web
Important to note: In a more recent report, it has been claimed that there is evidence that the leaked database is actually a re-use of an older 2019 Facebook leak.
Phishing, Vishing and Smishing expected to rise amid data breach
Once cybercriminals have access to phone numbers that are then sold on, attacks such as vishing or smishing are likely to follow. Vishing is a form of social engineering attack where a victim is duped into giving information over the phone, while smishing is conducted through SMS. With millions of records available to buy, it is highly likely these types of attacks will increase. It is also possible that hackers could access other online services using the phone number, which may have more damaging consequences.
Check Point Research has found an increase in phishing attacks around the holiday season, with a 17% rise in malicious emails during Black Friday and Cyber Monday. This year, Amazon Prime Day also saw an 86% increase in Amazon-related phishing emails.
Top Principles to follow in order to remain safe
- Avoid Clicking Links: Links in text messages are difficult to verify due to link shortening and the inability to hover over links to see targets. Instead of clicking on links in text messages, browse directly to the target site.
- Install Apps from Appstores: Smishing attacks may be designed to trick recipients into installing malicious apps on their mobile devices. Always install apps from reputable app stores, ideally after verifying their authenticity on the creator’s website.
- Do not Provide Data: Smishing attacks are commonly designed to steal sensitive data from their targets under the guise of verifying identities or other pretexts. Never provide personal data to someone that you have not called or texted via a number listed on their website.
- Always Verify Phone Numbers: Vishers will call while pretending to be from a legitimate organization. Before giving any personal data or doing anything that the attacker says, get the caller’s name and call them back using the official number from the company website. If the caller tries to talk you out of doing so, it is probably a scam.
- Never Provide Remote Computer Access: Vishers may request remote access to your computer to “remove malware” or fix some other issue. Never provide access to your computer to anyone except verified members of the IT department.
- Deploy Email Security Solutions: Modern email filtering solutions can protect against malware and other malicious payloads in email messages. Solutions can detect emails that contain malicious links, attachments, spam content, and language that could suggest a phishing attack. Email security solutions automatically block and quarantine suspicious emails and use sandboxing technology to “detonate” emails to check if they contain malicious code.
Check Point offers a range of solutions that can help organizations to mitigate vishing, phishing, and other related attacks. Check Point’s Harmony Email and Office includes anti-phishing protections and can help detect attempted data exfiltration inspired by a vishing attack. To learn more about how Check Point can protect your organization against social engineering threats, you’re welcome to request a free demo today.
-Ends-