Dubai-UAE – ESET researchers have recently discovered that the attackers behind Plead malware have been distributing it using compromised routers and man-in-the-middle (MitM) attacks against the legitimate ASUS WebStorage software. The new activity was detected by ESET in the territory of Taiwan, where Plead malware is most actively deployed. It was previously reported that Plead malware is used by the BlackTech group in targeted attacks, primarily those focused on cyberespionage in Asia.
In late April 2019, ESET researchers utilizing ESET telemetry observed multiple attempts to deploy this malware in an unusual way. Specifically, the Plead backdoor was created and executed by a legitimate process named AsusWSPanel.exe. This process belongs to a client for a cloud storage service called ASUS WebStorage. The executable file was digitally signed by the ASUS Cloud Corporation.
ESET suspects this is very likely to be a man-in-the-middle attack scenario, as the author of this research, ESET’s Anton Cherepanov, explains: “The ASUS WebStorage software is vulnerable to this type of attack. Namely, the software update is requested and transferred using HTTP; once an update is downloaded and ready to execute, the software doesn’t validate its authenticity before execution. Thus, if the update process is intercepted by attackers, they are able to push a malicious update.”
According to previously reported research on the topic, Plead malware also compromises vulnerable routers and even uses them as C&C servers for the malware. “Our investigation uncovered that most of the affected organizations have routers made by the same producer; moreover, the admin panels of these routers are accessible from the internet. Thus, we believe that a MitM attack at the router level is the most probable scenario,” adds Anton Cherepanov. He also offers a piece of advice: “It is very important for software developers to not only thoroughly monitor their environment for possible intrusions, but also to implement proper update mechanisms in their products that are resistant to MitM attacks.”
A possible second explanation scenario is a supply chain type of attack. Attacks on supply chains open unlimited opportunities for attackers to stealthily compromise large numbers of targets at the same time. However, as the ESET research blog post elaborates, it is less likely to be the case, even though it cannot be fully discounted.
Man-in-the-middle attack scenario infographic
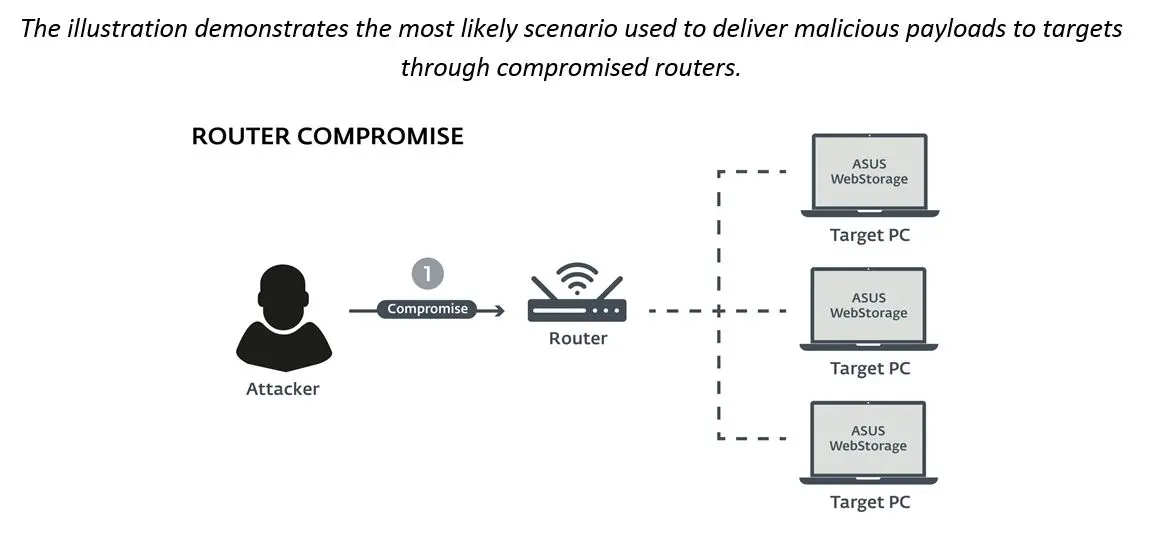

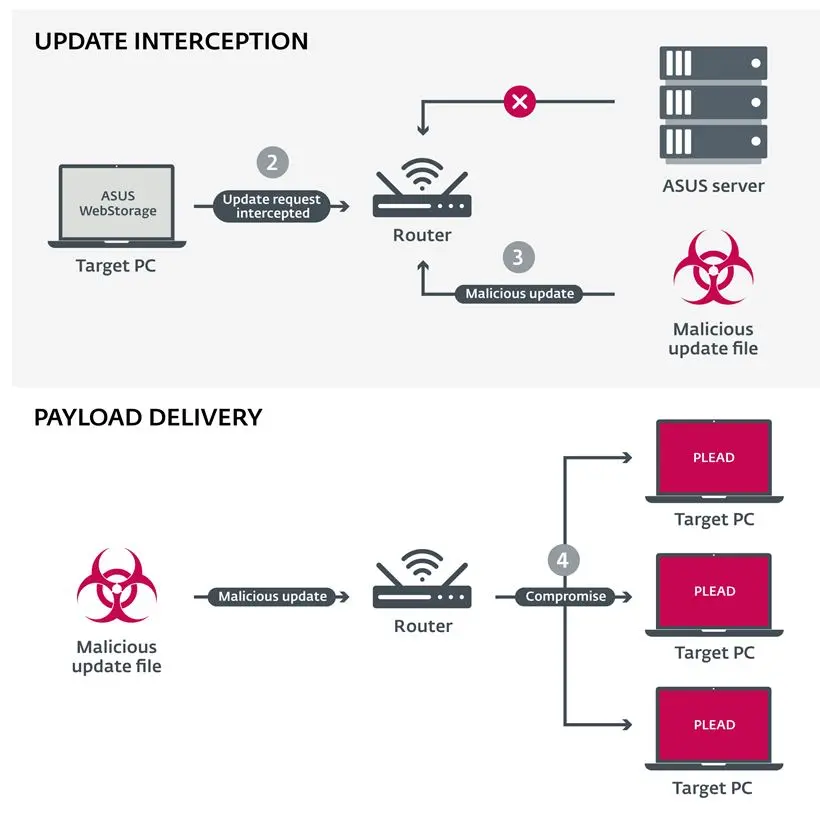

About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint and mobile security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give consumers and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in realtime to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D centers worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003. For more information, visit www.eset.com or follow us on LinkedIn, Facebook and Twitter.
For further information:
Vistar Communications
PO Box 127631
Dubai, UAE
E-Mail: hazem@vistarmea.com
Disclaimer: The contents of this press release was provided from an external third party provider. This website is not responsible for, and does not control, such external content. This content is provided on an “as is” and “as available” basis and has not been edited in any way. Neither this website nor our affiliates guarantee the accuracy of or endorse the views or opinions expressed in this press release.
The press release is provided for informational purposes only. The content does not provide tax, legal or investment advice or opinion regarding the suitability, value or profitability of any particular security, portfolio or investment strategy. Neither this website nor our affiliates shall be liable for any errors or inaccuracies in the content, or for any actions taken by you in reliance thereon. You expressly agree that your use of the information within this article is at your sole risk.
To the fullest extent permitted by applicable law, this website, its parent company, its subsidiaries, its affiliates and the respective shareholders, directors, officers, employees, agents, advertisers, content providers and licensors will not be liable (jointly or severally) to you for any direct, indirect, consequential, special, incidental, punitive or exemplary damages, including without limitation, lost profits, lost savings and lost revenues, whether in negligence, tort, contract or any other theory of liability, even if the parties have been advised of the possibility or could have foreseen any such damages.



















