PHOTO
Dubai:— Group-IB, a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime, has presented a comprehensive overview of the cyber threat landscape in the Middle East and Africa (MEA) for the years 2023/2024 with the release of its annual Hi-Tech Crime Trends report. The report provides a thorough analysis of how cybersecurity challenges in the MEA region have evolved. In 2023, Group-IB's researchers identified a 68% surge in the number of ransomware attacks, with financial services and real estate companies emerging as the most common victims. The Gulf Cooperation Council (GCC) countries, South Africa, and Turkey were the most frequently targeted locales by Ransomware-as-a-Service (RaaS) affiliates. Information stealers pose a significant concern, impacting 297,106 infected devices in the MEA region whose logs were made available on Underground Clouds of Logs (UCL), and an additional 903,002 hosts, logs from which were put up for sale on underground markets. Additionally, 152 new data leaks were detected in the MEA region in 2023.
Nation-state sponsored hackers target MEA
Group-IB researchers discovered that the Middle East and Africa was a significant target for advanced persistent threats (APTs), also known as nation-state sponsored groups, last year. Overall, Group-IB attributed 523 attacks to nation-state actors across the globe in 2023. Attacks on MEA organizations accounted for 15% of the global total, numbering 77, with Group-IB experts asserting that this may be due to ongoing geopolitical conflicts in the region, along with MEA’s importance to the global energy market.
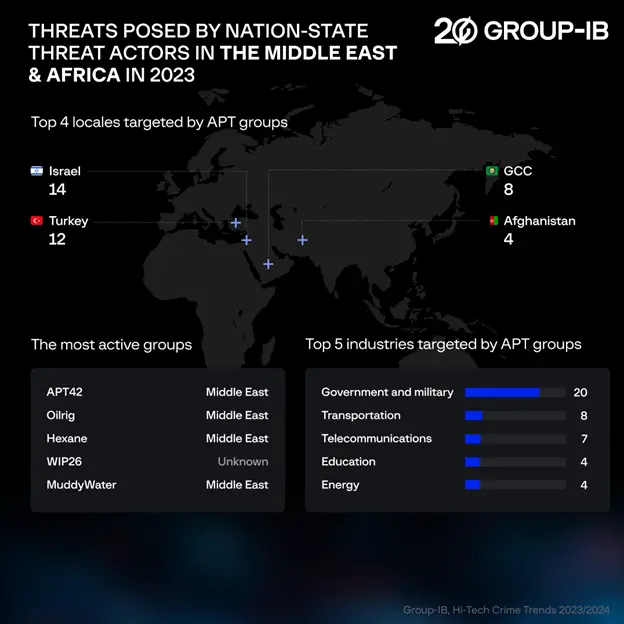

The top targeted locales in the MEA region in 2023 were Israel (14 attacks), Turkey (12) and the GCC region (8). Government and military organizations suffered the most APT attacks in the MEA region, totalling 20. Transportation (8 attacks) and telecommunications (7) were the second and third most targeted sectors, respectively.
Attacks coordinated by groups such as APT42, Oilrig and Hexane (all from MEA) reflect the desire of certain countries in the region to strengthen their influence through espionage. Groups from East Asia, including IronTiger and APT10, demonstrated that they had the ability to conduct large-scale cyber operations targeting various sectors of the economy and public administration.
Ransomware chronicles: the storm continues in 2023
The proliferation of ransomware attacks persisted last year, with an escalating number of companies experiencing the compromise of their critical systems and the exposure of their sensitive information. Last year, Group-IB identified 205 companies in the MEA region that had their information published on ransomware Data Leak Sites (DLSs), which translates to an approximate 68% increase from the previous year when information belonging to 122 victim companies appeared on DLSs.
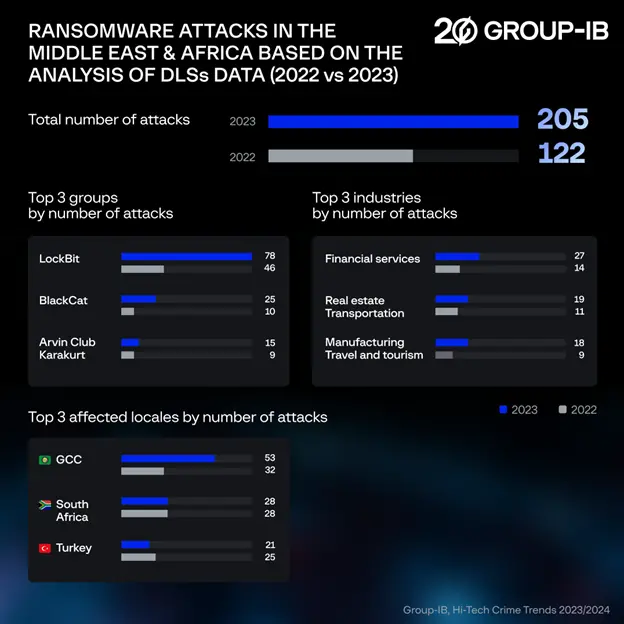

In 2023, the financial services sector remained the most often targeted in the region, accounting for 13% of all victim companies whose data was posted on DLSs. The real estate industry ranked second and was involved in 9% of all attacks in the region. The manufacturing followed in third place and was also targeted in 9% of attacks.
Regarding the most active ransomware gangs in the region, LockBit was once again the most prolific with 38% of all victims in the MEA region whose data was posted on DLSs. BlackCat (ALPHV) came in second, with 12% of the attacks. Arvin Club ranked third, accounting for 7% of all ransomware attacks in MEA.
In 2023, the GCC (number one in the list of most frequent targets) experienced a substantial 65% increase in ransomware victims published on DLSs, rising from 32 in 2022 to 53 last year. The number of South African countries that appeared on DLSs was stable in both years, coming in at 28 in 2022 and 2023. The ransomware threat landscape in Iran escalated severely in 2023, growing from 2 victims in 2022 to 19 in 2023. Similarly, the number of Israel-based companies that appeared on DLSs in 2023 was threefold higher than in the preceding year, rising from 6 to 18. It’s worth noting that the actual number of ransomware attacks is believed to be significantly higher as many victims chose to pay the ransom and some ransomware gangs do not use DLS.
H.E. Dr. Mohamed Al Kuwaiti, Head of Cybersecurity for the UAE Government, said: “In an era when technology is evolving constantly, the UAE stands at the forefront of digital transformation. We have made great strides in safeguarding our digital landscape. However, ransomware remains a significant threat to our nation. Additionally, cybercriminals are adopting artificial intelligence to launch more advanced and sophisticated cyberattacks. This technology, once associated primarily with state and non-state actors, is now employed by a broader spectrum, including hacktivists. We, therefore, urge everyone - companies, public sector organizations and regulators, cybersecurity vendors, and law enforcement agencies - to collaborate and take the measures needed to stay ahead of cyber threats.”
Bear market: broker activity slows
Ransomware enablers who sell initial access to corporate networks on the Dark Web, known as Initial Access Brokers (IABs), adapting to the demands of other threat actors in the MEA region, experienced a slight downturn. In 2023, access to corporate networks of companies in MEA was offered for sale 173 times, marking a 9% decrease compared to the previous year's 191 instances in 2022. This decline could be attributed to the fact that more brokers are now directly engaging in RaaS operations.
The most affected sector in terms of access offers to compromised networks in 2023 in this region was the military-industrial complex and government organizations (13% of all offers targeting the region). The financial services sector came second (10% of all access offers targeting the region). The telecommunications, professional services, and manufacturing industries were joint-third, each accounting for 6% of access offers.
In terms of affected locales, the GCC is in the lead with 54 instances of access put up for sale, which accounts for 31% of all offers detected in the region by Group-IB analysts, although this figure was 29% lower than in 2022. The number of offers of initial access to corporate networks in Israel grew by 150% in 2023, while Tunisia experienced a 67% rise.
Raccoon and friends stealing things
Logs of information stealers have become one of the main ways for cybercriminals to gain access to company networks because they are simple, yet very effective. Information stealers are a type of malware that collects credentials saved in browsers, bank card details, crypto wallet information, cookies, browsing history, and other information from browsers installed on infected computers.
Free Underground Clouds of Logs (UCL) are one of the main sources of data about infected hosts. Over the past year, there has been a 52% increase in the number of unique infected hosts in the MEA whose logs have been published on UCLs, reaching nearly 300,000. Turkey and Egypt remain the most often attacked countries in the MEA region.
Underground markets are also on the rise. Unlike UCLs, where a large part of logs is distributed free of charge, underground markets are always used to sell logs from hosts compromised by information stealers. In 2023 there was a 58% increase compared to 2022, and the total number of hosts put up for sale and related to the MEA region was 903,002. Egypt is also the main target, based on the logs found on underground markets with 160,006 logs detected in 2023. Raccoon, LummaC2, RedLine Stealer, and Vidar were the most popular information stealers among cyber criminals targeting the region.
Carding market slumps
Unlike other global regions that experienced a resurgence, the MEA illicit carding market continued a trend over the past few years trending towards a slowdown. In 2023, Group-IB’s researchers noted only a 2% increase in the number of compromised cards issued by banks in the MEA region.
The GCC experienced a notable 36% increase in compromised cards, rising from 98,339 in 2022 to 133,320 in 2023. In Turkey, the number of detected compromised cards increased by 13% to 77,611, while in South Africa, the 2023 figure fell by 22% from 71,770 to 56,317 in 2023. Egypt witnessed a notable increase, with compromised cards reaching 18,499, up 154% from the preceding year.
Tide of leaks
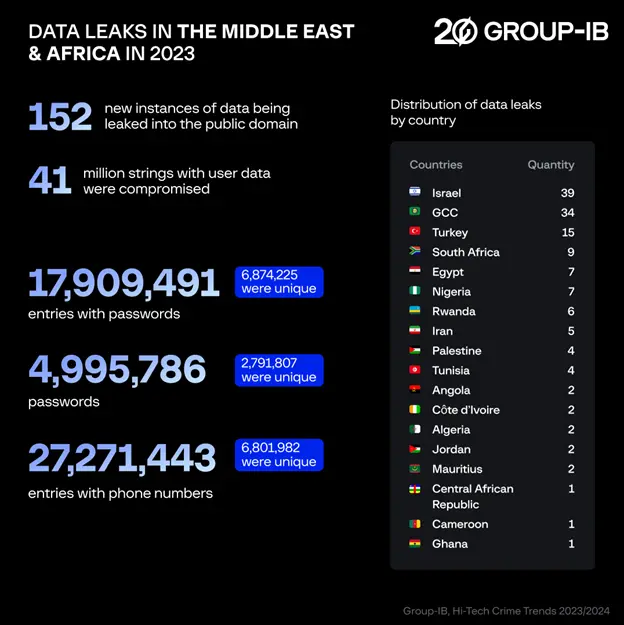
In 2023, 152 new instances of data being leaked into the public domain were detected in the MEA region. As part of these incidents, more than 41 million strings with user data were compromised. Israel, the GCC, and Turkey were hit the hardest, with 39, 34, and 15 instances of data leakage, respectively.

"Amidst the rapid digital transformations across the Middle East and Africa, cybersecurity remains paramount. The evolving threat landscape presents significant challenges for organizations, emphasizing the critical need to foster a robust culture of cybersecurity. By prioritizing proactive measures and collaboration, companies can fortify their defenses against the diverse array of cyber threats, including ransomware, APT attacks, and data leaks, all of which lurk in our region. Group-IB is committed to empowering organizations in the MEA region with cutting-edge cybersecurity technologies and expertise to navigate these challenges effectively and safeguard their digital assets,” Ashraf Koheil, Regional Sales Director META at Group-IB, said.
Group-IB’s Hi-Tech Crime Trends 23/24 highlights shifts in threat actor behaviors, the emergence of new TTPs, and the overarching trends that have come to define the evolving nature of cybersecurity threats. You can download the report by clicking here.
About Hi-Tech Crime Trends report
Group-IB has been presenting its annual reports since 2012, integrating data gathered as a result of the company’s own investigations with incident response findings worldwide. Serving as a practical guide for a wide range of experts — in risk management, digital business transformation, strategic planning in the cybersecurity field and investing in information system protection — the report provides annual forecasts that have always proved to be accurate. For technical specialists, including СISOs, SOC and DFIR teams, researchers and malware analysts, as well as Threat Hunting experts, Group-IB’s report provides an opportunity to analyze the relevance of cybersecurity policies, adjust security settings for their systems and strengthen their expertise in countering cyberthreats relevant to their industry.
This year, Group-IB implemented a number of significant improvements to its Hi-Tech Crime Trends report in order to deliver more precise and relevant information to its readers. Group-IB has firstly revised its reporting timeframe to compare calendar years. The second major enhancement has seen Group-IB provide region-specific strategic intelligence in each chapter. Further new additions include a dedicated section discussing AI threats, and a deep dive into the ways cybercriminals are abusing legitimate services.
Thanks to the use of unique tools for tracking the infrastructure of cybercriminals, as well as a thorough study of research by various cybersecurity teams worldwide, Group-IB experts annually identify and confirm common patterns that form a full picture of the development of cyberthreats in the world. This forms the basis of future forecasts set out in the report that help companies around the world build effective cybersecurity strategies based on relevant threats.
More analytics on Group-IB’s research hub.
-Ends-
About Group-IB
Founded in 2003 and headquartered in Singapore, Group-IB is a leading creator of cybersecurity technologies to investigate, prevent, and fight digital crime. Combating cybercrime is in the company’s DNA, shaping its technological capabilities to defend businesses, citizens, and support law enforcement operations.
In November 2023, Group-IB will celebrate the 20th anniversary of its founding with a range of exciting events marking the company’s global growth and significant contribution to international law enforcement efforts aimed at stamping out cybercrime.
Group-IB’s Digital Crime Resistance Centers (DCRCs) are located in the Middle East, Europe, Asia-Pacific, and Central Asia to help critically analyze and promptly mitigate regional and country-specific threats. These mission-critical units help Group-IB strengthen its contribution to global cybercrime prevention and continually expand its threat-hunting capabilities.
Group-IB’s decentralized and autonomous operational structure helps it offer tailored, comprehensive support services with a high level of expertise. We map and mitigate adversaries' tactics in each region, delivering customized cybersecurity solutions tailored to risk profiles and requirements of various industries, including retail, healthcare, gaming, financial services, manufacturing, critical services, and more.
The company’s global security leaders work in synergy with some of the industry’s most advanced technologies to offer detection and response capabilities that eliminate cyber disruptions agilely.
Group-IB's Unified Risk Platform (URP) underpins its conviction to build a secure and trusted cyber environment by utilizing intelligence-driven technology and agile expertise that completely detects and defends against all nuances of digital crime. The platform proactively protects organizations’ critical infrastructure from sophisticated attacks while continuously analyzing potentially dangerous behavior all over their network.
The comprehensive suite includes the world’s most trusted Threat Intelligence, The most complete Fraud Protection, AI-powered Digital Risk Protection, Multi-layered protection with Managed Extended Detection and Response (XDR), All-infrastructure Business Email Protection, and External Attack Surface Management.
Furthermore, Group-IB's full-cycle incident response and investigation capabilities have consistently elevated industry standards. This includes the 70,000+ hours of cybersecurity incident response completed by our sector-leading DFIR Laboratory, more than 1,400 successful investigations completed by the High-Tech Crime Investigations Department, and round-the-clock efforts of CERT-GIB.
Its solutions and services have time and again been revered by leading advisory and analyst agencies such as Aite Novarica, Forrester, Frost & Sullivan, KuppingerCole Analysts AG, and more.
Being an active partner in global investigations, Group-IB collaborates with international law enforcement organizations such as INTERPOL, EUROPOL, and AFRIPOL to create a safer cyberspace. Group-IB is also a member of the Europol European Cybercrime Centre’s (EC3) Advisory Group on Internet Security, which was created to foster closer cooperation between Europol and its leading non-law enforcement partners.
For more information, please contact:
- pr@group-ib.com
- https://www.group-ib.com
- https://www.group-ib.com/blog




















