PHOTO
Kaspersky analysis has revealed that phishing attacks are becoming increasingly more targeted. A number of new tricks have also been found - from HR dismissal emails to attacks disguised as delivery notifications. As a result of such tendencies, security solutions have detected 2,578,501 phishing attacks in Egypt, UAE, Saudi Arabia, Qatar, Kuwait, Bahrain, and Oman. These and other findings are documented in Kaspersky’s new spam and phishing in Q2 2020 report.

Phishing is one of the oldest and most flexible types of social engineering attacks. They are used in many ways, and for different purposes, to lure unwary users to the site and trick them into entering personal information. The latter often includes financial credentials such as bank account passwords or payment card details, or login details for social media accounts. In the wrong hands, this opens doors to various malicious operations, such as money being stolen or corporate networks being compromised. This makes phishing a popular initial infection method.
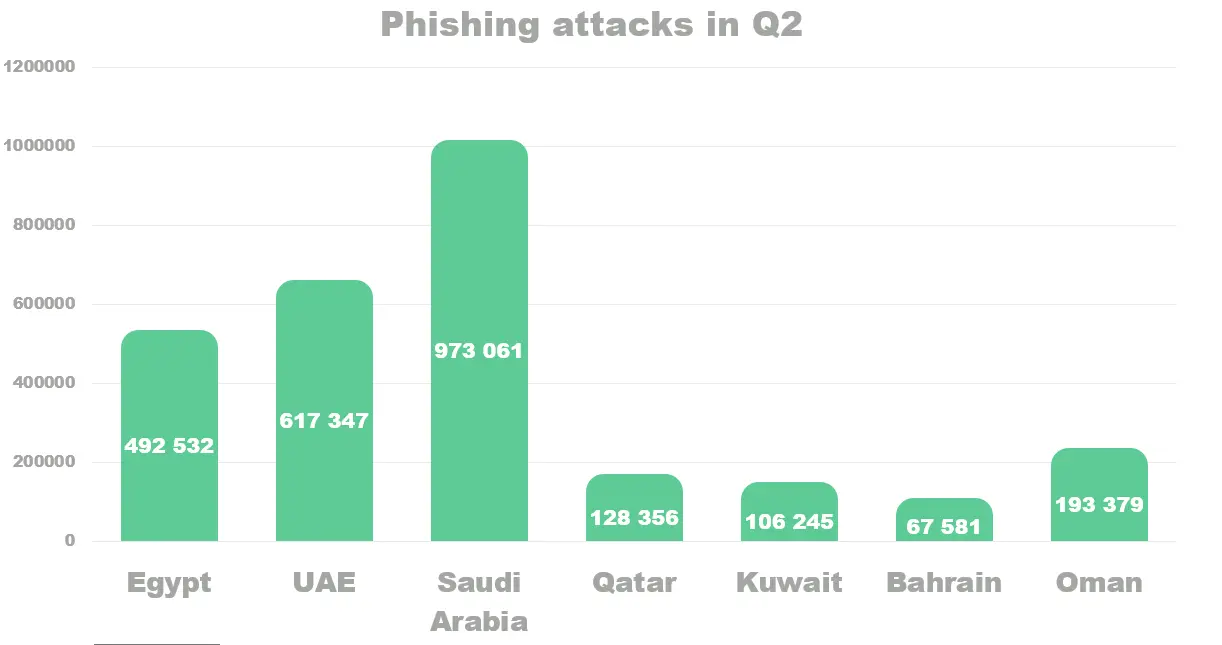
Users in Saudi Arabia have been influenced the most by this type of threat: there were 973, 061 phishing attacks detected in 3 months. It was followed by (UAE 617,347), Egypt (492,532), Oman (193,379), Qatar (128,356), Kuwait (106,245), Bahrain (67,581).
Phishing is a strong attack method because it is done at such a large scale. By sending massive waves of emails under the name of legitimate institutions or promoting fake pages, malicious users increase their chances of success in their hunt for innocent people’s credentials. The first six months of 2020, however, have shown a new aspect to this well-known form of attack.
Targeted attacks: small businesses in focus
As Kaspersky analysis has indicated, in Q2 2020, phishers increasingly performed targeted attacks, with most of their focus on small companies. To attract attention, fraudsters forged emails and websites from organizations whose products or services could be purchased by potential victims. In the process of making these fake assets, fraudsters often did not even try to make the site appear authentic.
Such targeted phishing attacks can have serious consequences. Once a fraudster has gained access to an employee's mailbox, they can use it to carry out further attacks on the company the employee works for, the rest of its staff, or even its contractors.
Jack of all trades: new tricks for old purposes
The news agenda, following the COVID-19 outbreak, has already influenced the “excuses” fraudsters use when asking for personal information. This included disguising their communications with unsuspecting users as:
- Delivery services. At the peak of the pandemic, organizations responsible for delivering letters and parcels were in a hurry to notify recipients of possible delays. These are the types of emails that fraudsters began to fake, with victims asked to open an attachment to find out the address of a warehouse where they could pick up a shipment that did not reach its destination.
- Postal services. Another relatively original move used by fraudsters was a message containing a small image of a postal receipt. The scammers expected that the intrigued recipient would accept the attachment (which, although it contained ‘JPG’ in the name, was an executable archive) as the full version and decide to open it. The Noon spyware was found in mailings such as these examined by Kaspersky researchers.
- Financial services. Bank phishing attacks in the second quarter were often carried out using emails offering various benefits and bonuses to customers of credit institutions due to the pandemic. Emails received by users contained a file with instructions or links to get more details. As a result, depending on the scheme, fraudsters could gain access to users’ computers, personal data, or authentication data for various services.
- HR services. The weakening of the economy during the pandemic in a number of countries caused a wave of unemployment, and fraudsters did not miss this opportunity to strike. Kaspersky experts encountered various mailings that announced, for example, some amendments to the medical leave procedure, or surprised the recipient with the news about their dismissal. In some attachments, there was a Trojan-Downloader.MSOffice.SLoad.gen file. This Trojan is most often used for downloading and installing encryptors.
“When summarizing the results of the first quarter, we assumed that COVID-19 would be the main topic for spammers and phishers for the past few months. And it certainly happened. While there was the rare spam mailing sent out without mentioning the pandemic, phishers adapted their old schemes to make them relevant for the current news agenda, as well as come up with new tricks,” comments Tatyana Sidorina, security expert at Kaspersky.
Read more about the new phishing techniques on Securelist.
Kaspersky experts advise users to take the following measures to protect themselves from phishing:
- Always check online addresses in unknown or unexpected messages, whether it is the web address of the site where you are being directed, the link address in a message and even the sender’s email address, to make sure they are genuine and that the link in the message doesn’t hide another hyperlink.
- If you are not sure that the website is genuine and secure, never enter your credentials. If you think that you have may have entered your login and password on a fake page, immediately change your password and call your bank or other payment provider if you think your card details were compromised.
- Use a proper security solution with behavior-based anti-phishing technologies, such as Kaspersky Security Cloud and Kaspersky Total Security, which will warn you if you are trying to visit a phishing web page.
About Kaspersky
Kaspersky is a global cybersecurity company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 250,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
For further information, please contact:
Sweta Fernandes, Account Executive, Golin, KasperskyTeam@golin.ae
© Press Release 2020
Disclaimer: The contents of this press release was provided from an external third party provider. This website is not responsible for, and does not control, such external content. This content is provided on an “as is” and “as available” basis and has not been edited in any way. Neither this website nor our affiliates guarantee the accuracy of or endorse the views or opinions expressed in this press release.
The press release is provided for informational purposes only. The content does not provide tax, legal or investment advice or opinion regarding the suitability, value or profitability of any particular security, portfolio or investment strategy. Neither this website nor our affiliates shall be liable for any errors or inaccuracies in the content, or for any actions taken by you in reliance thereon. You expressly agree that your use of the information within this article is at your sole risk.
To the fullest extent permitted by applicable law, this website, its parent company, its subsidiaries, its affiliates and the respective shareholders, directors, officers, employees, agents, advertisers, content providers and licensors will not be liable (jointly or severally) to you for any direct, indirect, consequential, special, incidental, punitive or exemplary damages, including without limitation, lost profits, lost savings and lost revenues, whether in negligence, tort, contract or any other theory of liability, even if the parties have been advised of the possibility or could have foreseen any such damages.




















