According to Kaspersky’s (https://Kaspersky.co.za/) latest research on the threat landscape trends, South Africa, Kenya and Nigeria are facing a dramatic change in the threat landscape. While regular, self-propagating malware is decreasing dramatically, as it is no longer effective and cannot fly under security radars, the region will see the growth of new cybercrime models in the upcoming year.
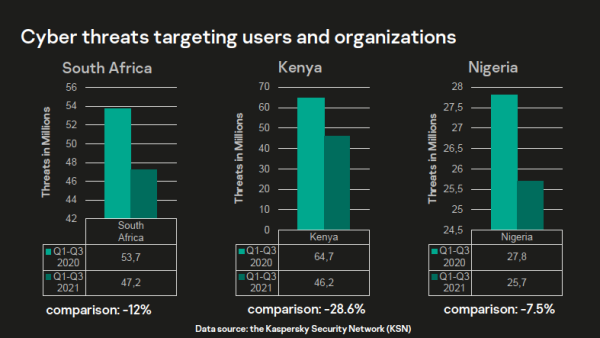
While comparing the overall number of mass cyberattacks in 2021, security researchers at Kaspersky noticed a 7,5% decrease in Nigeria, 12% decrease in South Africa and an unprecedented 28,6% decrease in Kenya. The reason for such a change was the introduction and popularisation of new cybercrime models in the region, with cybercrime tools becoming more targeted along with a long running trend where malware creators rely not on the technical advantage of their technologies over security protection, but on the human factor. This has stimulated the evolution of phishing schemes in 2021. In particular, the region saw a wave of ‘Anomalous’ spyware attacks.
The usual phishing spyware attack begins when attackers infect a victim by sending them an e-mail with a malicious attachment or a link to a compromised website and ends when the spyware is downloaded and activated on the victim’s device. Having gathered all necessary data, the operator usually ends the operation by attempting to leave the infected system unnoticed. In the anomalous attacks, however, the victim’s device becomes not only a source of data but also a tool for spyware distribution. Having access to the victim’s email server, the malware operators use it to send phishing emails from a legitimate company’s email address. In this case, anomalous spyware attacks an organisation’s server for collecting stolen data from another organisation and sending further phishing emails.
“The Anomalous spyware attacks have a huge potential for growth in South Africa, Kenya and Nigeria in 2022, because unlike regular spyware the entry level for attackers who wish to employ this tactic is significantly lower - since instead of paying for their own infrastructure, they abuse and employ the victims’ resources. We see that cheaper attack methods have always been on the rise in the region and cybercriminals quickly pick up on new tactics. Kaspersky therefore suggests that in the nearest future, these countries should be prepared for such attacks”, says Maria Garnaeva, Senior Security Researcher at Kaspersky ICS CERT team.
However, the mass scale attacks are not disappearing, but rather transforming. Garnaeva also reports on a mass-scale and pervasive fake installers campaigns, where fake pirated software sites serve up malware as a service. The scheme is usually the following: a user searches for a free version of an extremely popular legitimate spyware. The cybercriminals are offering them a fake installer using ‘black SEO technic’ – the abuse of the legitimate search engines, resulting in the offering of the fraudulent websites first. As a result of software installer execution, a few dozen malware samples are downloaded and installed with a goal of turning the infected devices into a part of the Glupteba botnet. The whole fake installers campaign and botnet has been extremely active in South Africa in 2021 and continues to evolve, yet it is scarcely researched.
“While the Glupteba botnet seems to be a threat for consumers, we are still researching it and keeping an eye on its behaviour, since some distributed malware resembles APT-related samples like Lazarus APT groups and were recently used in the largest DDoS attack in Russia. It is too early to say it with a high level of confidence, but these factors may suggest that we are now entering the era where APT actors start to use existing malware distribution platforms which makes an attribution of such attacks harder and opens a new vector similar to supply chain attacks,” adds Garnaeva.
In order to stay protected from such new cybercrime models and threats, Kaspersky recommends the following:
- Pay close attention to and don’t open any suspicious files or attachments received from unknown sources.
- Do not download and install applications from untrusted sources.
- Do not click on any links received from unknown sources and suspicious online advertisements.
- Create strong passwords and don’t forget to change them regularly.
- Always install updates. Some of them may contain critical security issues fixes.
- Ignore messages asking to disable security systems for office software or antivirus software.
- Use a robust security solution appropriate to your system type and devices, such as Kaspersky Internet Security (https://bit.ly/3nQQq4G) or Kaspersky Security Cloud (https://bit.ly/3nNj8U7).
For further information please contact:
Sandy Greaves Campbell | INK&Co.
Cell: +27 83 408 3373
sandy@inkandco.co.za
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.Kaspersky.co.za.
Follow:
Facebook: bit.ly/3DDVuPC
Twitter: bit.ly/38x6EHE
YouTube: bit.ly/3yx5oPp
Instagram: bit.ly/2WFGBLM
Blog: bit.ly/3gPs6MS
Disclaimer: Please note that INK&Co. utilise the services of content distribution company lists, which are subscriber based and updated regularly. To unsubscribe from receiving news and/or press releases from INK&Co. please email unsubscribe@inkandco.co.za.
© Press Release 2021
Disclaimer: The contents of this press release was provided from an external third party provider. This website is not responsible for, and does not control, such external content. This content is provided on an “as is” and “as available” basis and has not been edited in any way. Neither this website nor our affiliates guarantee the accuracy of or endorse the views or opinions expressed in this press release.
The press release is provided for informational purposes only. The content does not provide tax, legal or investment advice or opinion regarding the suitability, value or profitability of any particular security, portfolio or investment strategy. Neither this website nor our affiliates shall be liable for any errors or inaccuracies in the content, or for any actions taken by you in reliance thereon. You expressly agree that your use of the information within this article is at your sole risk.
To the fullest extent permitted by applicable law, this website, its parent company, its subsidiaries, its affiliates and the respective shareholders, directors, officers, employees, agents, advertisers, content providers and licensors will not be liable (jointly or severally) to you for any direct, indirect, consequential, special, incidental, punitive or exemplary damages, including without limitation, lost profits, lost savings and lost revenues, whether in negligence, tort, contract or any other theory of liability, even if the parties have been advised of the possibility or could have foreseen any such damages.


















