
After analyzing offers of malicious apps on Google Play that are for sale on the Darknet, Kaspersky experts have discovered that malicious mobile apps and store developer accounts are being sold at up to US$20,000. Using Kaspersky Digital Footprint Intelligence, researchers collected examples from nine different Darknet forums where the purchase and sale of goods and services related to malware is carried out. The report sheds light on how threats sold on the Darknet appear on Google Play and also reveals the offers available, price range and features of communication and agreements between cybercriminals.
Even though official app stores are vigorously policed, moderator services can’t always catch malicious apps before they’re uploaded. Every year a vast range of malicious apps are deleted on Google Play only after victims have been infected. Cybercriminals gather on the Darknet – a whole underground digital world with its own rules, market prices, and reputational institutions – to buy and sell Google Play malicious apps, and additional functions to upgrade and even advertise their creations.
Like on legitimate forums for selling goods, there are also various Darknet offers for different needs and customers with different budgets. To publish a malicious app, cybercriminals need a Google Play account and a malicious downloader code (Google Play Loader). A developer account can be bought cheaply, for US$200 and sometimes even for as little as US$60. The cost of malicious loaders ranges between US$2,000 and $20,000, depending on the complexity of malware, the novelty and prevalence of malicious code, as well as the additional functions.
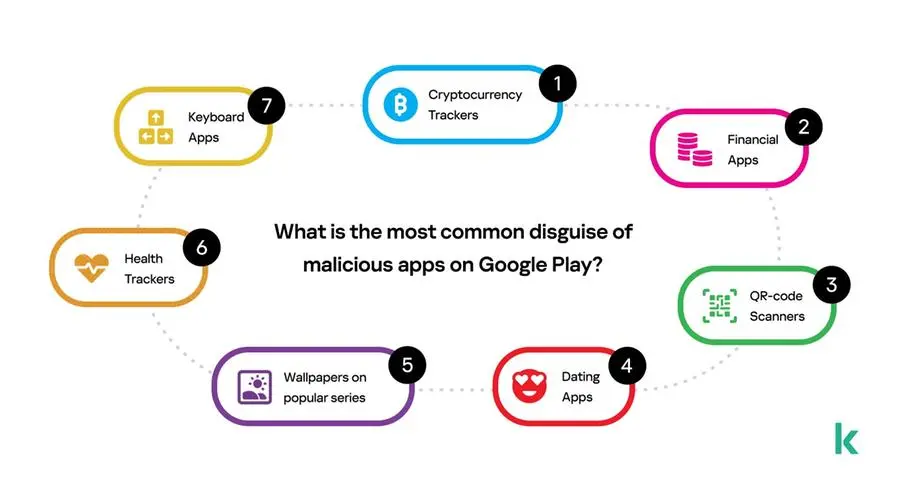
Most often, the malware being distributed is suggested to be hidden under cryptocurrency trackers, financial apps, QR-code scanners and even dating apps. Cybercriminals also highlight how many downloads the legitimate version of that app has, which means how many potential victims can be infected by updating the app and adding malicious code to it. Most frequently the suggestions specify 5,000 downloads or more.
For an additional fee, cybercriminals can obfuscate the application code to make it harder to detect by cybersecurity solutions. To increase the number of downloads to a malicious app, many attackers also offer to purchase installs - directing traffic through Google ads and attracting more users to download the app. Installs cost differently for each country. The average price is US$0.50, with offers ranging from US$0.10 to several dollars. In one of the discovered offers, advertisements for users from the USA and Australia cost the most - US$0.80.
Fraudsters offer three kinds of work: for a share of the final profit, rent, and full purchase of either an account or a threat. Some sellers even hold auctions to buy their goods, since many sellers limit the number of lots sold. For example, in one offer that was found, the starting price was US$1,500, with $700 incremental steps in the auction, and the blitz - the instant purchase for the highest price - was $7,000.
Darknet sellers can also offer to publish the malicious app for the buyer so they do not directly interact with Google Play, but can still remotely receive all of the victims' detected data. It may seem that in such a case the developer can easily deceive the buyer, but it is common among Darknet sellers to preserve and maintain their reputation, promise guarantees, or accept payment after the terms of the agreement have been completed. To reduce risks when making deals cybercriminals often resort to the services of disinterested intermediaries, known as “escrow”. The escrow may become a special service and supported by a shadow platform, or a third party who is not interested in the results of the transaction.
“Malicious mobile apps continue to be one of the top cyberthreats targeting users, with more than 1.6 million mobile attacks detected in 2022. At the same time, the quality of cybersecurity solutions that protect users from these attacks is also increasing. On the Darknet, we found messages from cybercriminals complaining how it is now much harder for them to upload their malicious apps to official stores. However, this also means that they will now come up with much more sophisticated circumvention schemes, so users should stay alert and carefully check which apps they are downloading,” comments Alisa Kulishenko, security expert at Kaspersky.
Find more examples of threats on Google Play sold on Darknet in the full report on Securelist.
To stay safe from any mobile threats, Kaspersky recommends:
- Check the permissions of the apps that you use and think carefully before permitting an app, especially when it comes to high risk permissions such as permission to use Accessibility Services. The only permission that a flashlight app needs is to the flashlight (which doesn’t even involve camera access).
- A reliable security solution can help you to detect malicious apps and adware before they can start behaving badly on your device.
- iPhone users have some privacy controls provided by Apple, and users can block app access to photos, contacts and GPS features if they think those permissions are unnecessary.
- Update your operating system and important apps as updates become available. Many safety issues can be solved by installing updated versions of software.
- To inquire about threat monitoring services for your organization, please contact us at dfi@kaspersky.com.
-Ends-
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at https://me-en.kaspersky.com/
Media Relations
Amine Mneimne
amneimne@golin-mena.com
Golin MENA, Dubai



















